Walt Disney recently announced a new service called MoviesAnywhere, aiming to link all your purchased videos from other vendors into one streaming service. Yes, this is pretty much what Disney meant when it announced it would be making its own streaming service. They’re retiring the old “Disney Movies Anywhere” service (which maybe didn’t quite make it clear it includes PG-13 titles from Marvel alongside the G-rated talking animals).
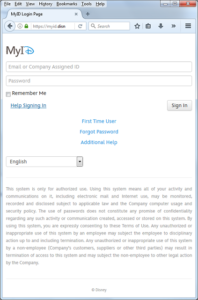
The roll-out isn’t exactly perfect but hasn’t been a disaster. My personal experience was one of annoyance when I couldn’t login to the website using my Google account. I tried on a PC with Firefox, and on an Android device with Chrome. Eventually I figured out I needed to have 3rd party cookies enabled. Disney made the mistake of not documenting this on their website (it’s not even mentioned on their help page).
For Android users, you can link your iTunes account to MoviesAnywhere, but you can’t do it from the app on an Android device. You need access to iTunes to link the accounts, so it can be done from a Windows PC. I haven’t tested streaming of iTunes content on an Android device yet.
There’s a lot of other things I could nit-pick about the launch and opinions I can express, but what I really wanted to write about is unintentional leaking of sensitive but not private information.
When I sent an e-mail to help@moviesanywhere.com with my issue, I got an automated response telling me my request was received and someone would get back to me shortly (no one ever did). It’s a simple e-mail, as you can see:
They even gave a handy ticket number to my case! With a link to click on, so I could check the status of the ticket! Man that’s customer service all right. Let’s just click on that link, which points at https://help.moviesanywhere.com/hc/requests/31125
Well that doesn’t look right. Am I supposed to create an account to view my ticket, ala salesforce.com? Gah! I hate making unnecessaryu accou– wait.
pretty sure we aren’t in Kansas anymore.
In fact, we’re on a Walt Disney Corporation corporate IT page for employees to do Single Sign-On. Doubtful this was what was intended by whatever poor shmuck was testing the MoviesAnywhere customer help ticketing system.
Alice: “Ok Bob, sending you another e-mail with a ticket.”
Bob: “Thanks. And yeah, I click it and hey the link works!”
Alice: “Well we’re in the office, maybe we should test it extenally to re-create the customer experience.”
Bob: “That sounds like a good QA step Alice, let’s just–”
PHB: “Nah, ship it!”
>_<
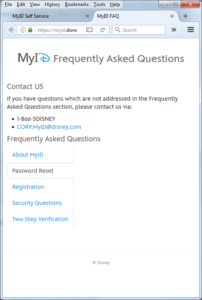
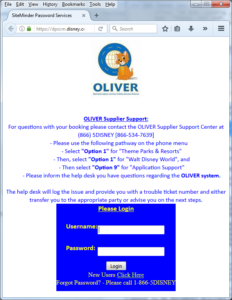
Of course, now we know 1-866-5DISNEY is a number for Disney employees to get IT help. And corp.myid@disney.com is an e-mail address staffed by Disney employees to help with issues related to corporate sign-ons. This isn’t secret information, as it’s actually all over the Internet, mentioned in various forums by Disney employees and probably known to many thousands of people. It’s not private data either, as it doesn’t purtain to an individual person but a business. But it’s still what we in InfoSec terms Sensitive. Because of the fun we can do with it by plugging these terms into a web search!
https://www.hybrid-analysis.com/sample/7b9889d352f914b3d5fa32256b5e58b9771aabf029fa1d61518a4ac75b0dd7e3
That page is part of a commercial sandboxing service, and shows the results of document scan. The document was part of an official Disney spearphishing test, to educate employees to stop clicking on everything alrea –ahem– But that’s just one of many funyuns we get. Here’s another one:
https://dpscm.disney.com/login.fcc
for a supply chain management system. It even contains a link to e-mail someone to gain access. You’d probably need to pull off some pretty good social engineering to manage access, but if you did there’s going to be a lot of sensitive data related to who has ordered what, from where, etc. But it’s not as promising, nor as telling, as this result:
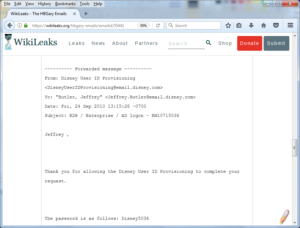
https://wikileaks.org/hbgary-emails/emailid/55441
which is on WikiLeaks as part of a document dump from the HB Gary hack by Anonymous in 2011. The particular e-mail gives insight into how the process works inside Disney for provisioning user credentials, and even the sort of initial password that may be assigned.
And over here we have:
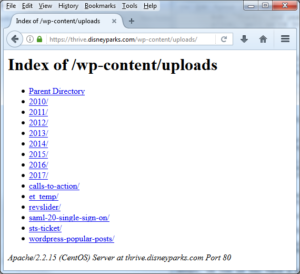
https://thrive.disneyparks.com/wp-content/uploads/2015/04/NewEmployeeOnboarding.doc
Woops.
Ok now we may have a problem. “Thrive” appears to be an internal group at Disney. In fact, one of the documents exposed here says:
Thrive is a learning website created by and for GM&S Cast Members, which offers tools to help you grow in your role.
with “GM&S” short for Global Marketing & Sales. If you attempt to access the main page it’ll re-direct you to Disney’s MyID login system. But Google was able to index a Word document, so clearly something isn’t quite right.
According to the webserver’s handy banner on that index page, we know the server is a CentOS system with Apache 2.2.15. Based on the Apache version, it’s likely CentOS 6. There’s a WordPress install obviously, and whoever put it in didn’t understand (or care) how to configure Apache to prevent directory indexing (or perhaps it was enabled to troubleshoot an issue and no one remembered to undo it). Based on the years in the uploads folder this has been up since 2010. Fortunately, none of the PHP scripts are accessible without going through the corporate authentication. But some content that’s probably not meant to be public has been browsable for as long as directory indexing has been enabled.
Except for a few folders, there really isn’t anything of consequence. But there are a number of Microsoft Word, Excel, and Adobe PDF documents intended for internal training and education. Some appear to be documents provided by 3rd party partners and vendors of Disney and may not be intended for public consumption.
The biggest risk of these kind of sensitive document leakages is for social engineering. Any red team will tell you how much they can use this sort of treasure trove to not only craft believable phishing attacks, but also pass themselves off as legitimate company represetnatives. Print out some of the PDF’s I found in here, put them in a binder, don some business attire and you can visit the corporate office of a Disney partner and claim your’re from corporate to do a training session. Hijinks ensue!
Ethically, I’m obliged to report this, which I did over a week ago. I sent e-mail to several Information Security related addresses within Disney, but never received more than an automated reply. I could just post this article and leave it at that, but due-dilligence obligates me to at least try some more.