Passwords Suck
Long ago I gave-up trying to remember all the passwords I use for websites. I used to be able to use the same few passwords everywhere (and they didn’t even have to be eight characters long). I didn’t use terrible passwords. Something like “v#kt0r!” was pretty good by standards in 2005. But cracking passwords, hash look-ups and brain-dead practices mean you can’t do that anymore. Did you have a super-secure long password on Sony’s Playstation Network back around 2011? Not anymore I bet.
Many people in the industry started suggesting using password templates or patterns, where you’d have the same basic password but tailor it per site. Or use the same password across financial sites, a different one for social sites, etc. Yet the issue was still the same when it came to breaches. The Anonymous hi-jinks on Twitter (I sort of miss the LulzSec logo…) didn’t help.
I decided to start using randomly generated passwords for most websites, relying on carefully selected passwords only for the most trusted and secure sites. Of course that meant not remembering my password for most sites. I’d need a password manager/vault/safe program. I decided to try out LastPass, a Windows application with an attached service that’d host all your (encrypted) passwords and could be synced via your account. I was a little wary of it but some conversations on Twitter and e-mail with people involved at LastPass made it seem like it was worth a go.
Within days of having installing LastPass and starting to use it, they announced that they had been backdoored.
Well…  !
!
To my knowledge the breach never resulted in any known pilfering of data, as LastPass hadn’t been foolish enough to actually store all their customers credential clear-text. Everything was heavily encrypted on the user’s end and supposedly the key only exists on your system. But it still made me pretty uneasy, and I was already not comfortable with the risk of entrusting my data to a 3rd party, even if it was encrypted. The second breach at LastPass in 2015 makes me feel justified in not using LastPass.
(Sidebar time, for those less experienced with encryption, cracking methods and the attack killchain; Even when data has been encrypted using a strong, reliable cipher with all the “best” practices, it can still be decrypted if someone gets the key. When the key is digital in nature and on the same sort of vulnerable systems we all use, well… The risk is along that of a patient dragon that hoards a vast trove of lead, waiting until that one foolish mortal walks in who happens to be carrying a Philosopher’s Stone.)
I looked for a solution similar to LastPass, but that wasn’t tied to a central server store, using proprietary ciphers or other nonsense. Bruce Schneir’s old standby of Password Safe was OK but relatively basic. It was also, at the time, closed source and Windows only. I often switched between Windows and Linux systems, and wanted to know that adopting a new platform wouldn’t shut me out of my password vault. I also didn’t want to pay for a commercial product: I’d bought and used SplashID since it was introduced on the Palm platform years ago, but they had a history of problems (updates would corrupt databases, sudden changes in the database format, frequent license-key issues). I also wanted to have integration with my web browser if possible.
Then I finally found KeePass. I was like:

You Should Be Using KeePass, Here’s Why
- KeePass is true Free Open-Source Software, and OSI Certified.
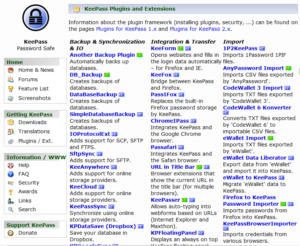
- It’s expandable via plugins:
- It uses many excellent security measures and principals such as strong RNG, memory protection, AES-256 ciphers and much more. The entire password database is encrypted (not just some fields) and stored locally.
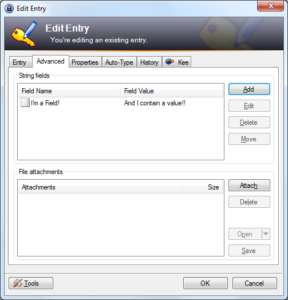
- Along with username and password fields, there are additional fields for URLs, notes and you can add as many extra fields as you need to any entry:
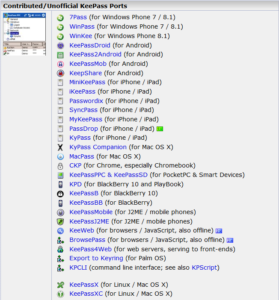
- It’s cross-platform with over 30 different contributed ports for around a dozen different computing platforms. And because it’s FOSS, future ports are entirely feasible:
- It’s very portable, with minimal dependencies and a single file store. The Windows version has no installer requirements and can be run from a flash drive. No registry changes are made, and no special uninstall procedure is needed. Database format is universal, so a KeePass installation on Linux can easily use a file originally created on Windows (or OSX, Linux, etc).
- KeePass is migration friendly. It has the ability to natively import passwords from common CSV formats, Password Safe v2, RoboForms, PassKeeper, 1Password Pro and other password managers. Thanks to plugins, many additional import (and export) formats are possible. Of course you can export your passwords too. These features not only support migrating, they increase inter-operability between groups that have different tool sets and needs.
- Oh! You can also use KeePass on Windows to automatically enter passwords into fields in browsers and other applications:
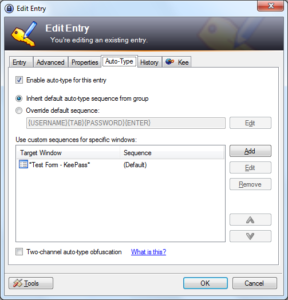
- Think not simply about webpages, but locally running applications. Automatic entry of credentials to your videogame, an encrypted PDF file, or any number of terrible legacy systems people have to deal with in a big corporate environment. Couple that with the Triggers feature in KeePass and you can automate workflows.
With all these features and more (password expiration, groups, digital key storage (via file attachments), optional key files for decryption, synchronization to files or URLs), KeePass is surprisingly Enterprise-ready. While it doesn’t offer some of the most advanced features of identity managment product suites such as CyberARK’s, much can be accomplished with judicious use of the feature’s in KeePass and some appropriate middle-ware. Need to have a system for your team to all be able to look-up passwords for sites, servers or whatnot? Just use KeePass. End-user OS is largely unimportant. Use an internal file repo system to keep changes synchronized or, if you’re more adventurous, install one of the plugins that supports synching to Dropbox, Google Drive, OneDrive, Amazon AWS, and others. Make use of password expiration settings so everyone knows when a critical system needs a new password, or an entry is out-of-date. Attach digital certificates or license keys to an entry and you can track all the licenses for your enterprise software, webserver SSL certificates and much more.
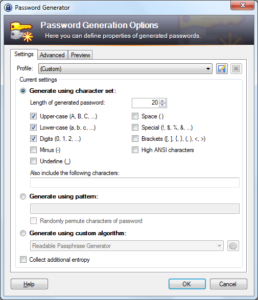
And it can generate passwords as well, in a highly customizable format: